Cardlytics & Publisher - CSA/SSO Implementation
Learn how to set up an SSO integration between Cardlytics and your IDP
Abstract
This document outlines the implementation of the Customer Service Application (CSA) tool, a platform designed to assist partner customer service representatives (CSRs) in resolving customer inquiries and processing escalations. It provides a step-by-step guide for publishers to set up Single Sign-On (SSO) integration with Cardlytics using an Identity Provider (IDP). Additionally, it details the process for secure rotation of application credentials, ensuring compliance with security protocols.
Overview
The CSA is a tool designed for partner CSRs to efficiently address customer concerns related to offer redemptions and manage escalations as needed. Cardlytics facilitates access to the CSA tool by configuring and providing a unique redirect URL for each financial institution. Publishers are required to integrate their IDP (e.g., Azure or Okta) with Cardlytics, ensuring secure and seamless access for designated users.
Implementation
Cardlytics will configure and provide a redirect url for accessing the CSA tool that is specific to a financial institution. The url will look something like this: https://csr.cardlytics.com/login?fi=[institutionId].
For example: https://csr.cardlytics.com/login?fi=7086
As a publisher, you'll need to provide the following:
-
client Id:
idp_client_id -
client secret:
idp_client_secret -
Issuer:
idp_issuer_urlwhere idp is from the Identity Provider (Azure or Okta).
Important
For whitelisting, you'll need to send Cardlytics your IP addresses for Production and PreProduction.
How It Works
Cardlytics will provide names and values for custom attributes (assigned_apps and application_scopes). As a publisher, you'll need to assign customer attributes for roles and access for each user who needs access to CSA. These attributes are typically added to the publisher's IDP (Azure or Okta, for example), as custom attributes that are sent back to Cardlytics in oAuth response.
-
application_scopes:Csr_Tier1_Users, Csr_Tier2_Users
-
All current CSA users who are part of the publisher team are designated as
Csr_Tier2_Usersin order to allow for creation and submission of tickets. -
assigned_apps = CSA
Cardlytics will provide you with a response url like this:
https://prod-publisher-management-v2.auth.us-east-1.amazoncognito.com/oauth2/idpresponse
PreProduction Configuration
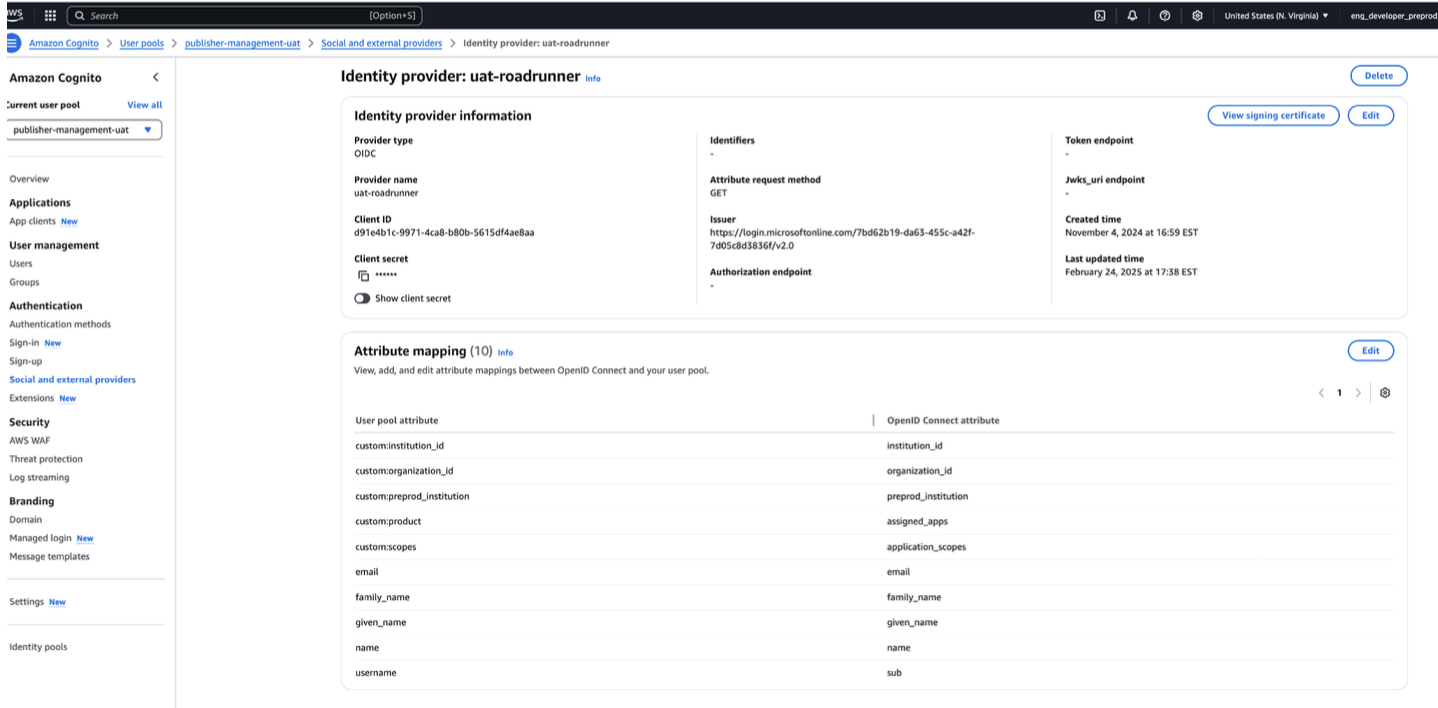
Production Playbook
Rotation Timeline
Your application client ID and secret will be rotated once a year.
Rotation Process
Notification of Upcoming Expiration
Responsible: Client
Prior to the expiration date, you will be informed about the pending expiration of the current client ID/secret.
Request for New Client ID/Secret
Responsible: Client
You formally request a new client ID and secret from your team.
Issuance of New Key
Responsible: Client
Upon approval, your team will generate a new client ID and secret.
A new key will be issued to your team.
Secure Transfer of New Key
Responsible: Client
You will securely send the new client ID and secret to Cardlytics using a secure email channel.
Secure Storage of New Key
Responsible: Cardlytics
Cardlytics will ensure that the newly issued client ID and secret are securely stored in a vault.
Key Rotation and Validation
Responsible: Cardlytics and the Client Change Control Team
The Client needs to reach out 45 days in advance to request Cardlytics product support with the key change and other details.
Summary
This document provides a comprehensive guide for publishers to implement CSA/SSO integration with Cardlytics, including key steps, configurations, and security processes:
- CSA Tool Access: Cardlytics supplies a financial institution-specific redirect URL for accessing the CSA tool.
- Publisher Requirements:
- Provide client credentials (
idp_client_idandidp_client_secret) and issuer URL. - Configure custom attributes (
assigned_apps,application_scopes) in the IDP for user roles and access levels.
- Provide client credentials (
- Key Rotation Process:
- Annual credential rotation is mandatory.
- The process involves notification, request, issuance, secure transfer, storage, and validation of new client credentials.
- PreProd Configuration and Contact:
- Publishers are advised to follow the provided production playbook and maintain communication with their designated Cardlytics point of contact.
The document emphasizes the importance of adhering to the outlined rotation timeline and process to maintain system security and operational integrity. Regular review and updates to the playbook ensure alignment with evolving security standards and protocols.
Updated about 2 months ago